We all have things we do regularly on our iPhones, whether it’s checking the weather, searching Google, or calling our congressperson to voice our displeasure. With iOS 14, Apple has opened up a new and customizable way of triggering such actions: Back Tap.
Back Tap is technically an accessibility feature for those who have trouble interacting with the iPhone physically. But just as curb cuts help both those in wheelchairs and those working on their sick ollies, the Back Tap feature is a boon for everyone.
With a double or triple tap on the back of any iPhone 8 or newer running iOS 14, you can invoke any one of a variety of actions, including custom Shortcuts. Unfortunately, Back Tap isn’t available in iPadOS 14.
Go to Settings > Accessibility > Touch > Back Tap (it’s way down at the bottom), where you can attach actions to both double tap and a triple tap.
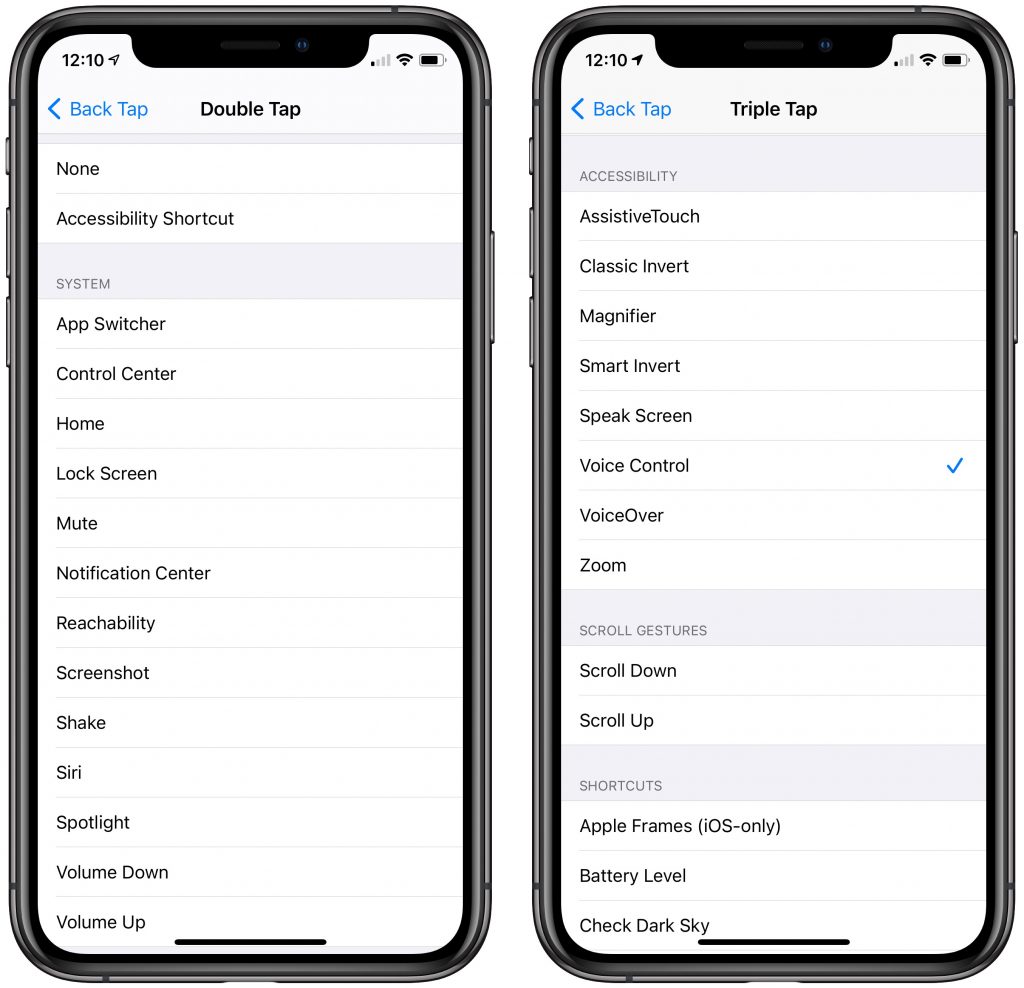
Apple provides a broad set of actions, but most of them are focused on helping people who can’t use other iPhone gestures. So yes, you could make a double tap open Spotlight for searching, but unless that’s somehow a lot easier than swiping down on the Home screen, it’s not worth one of your two triggers. Actions fall into four categories:
- System: Most of the System choices mimic easy Home screen gestures or button presses. Most interesting are Mute, which toggles the ringer volume without forcing you to press the Volume Down button repeatedly, and Screenshot, which takes a picture of your screen without requiring you to press two buttons at once.
- Accessibility: For those who need these Accessibility options, having them easily accessible via Back Tap will be welcome. The most compelling actions for the general public are Magnifier, Speak Screen, and Voice Control. (Voice Control provides much more capable dictation than Siri.)
- Scroll Gestures: These options scroll a vertically oriented page or screen. Sadly, they don’t work for horizontally driven page flipping in book reading apps like Libby.
- Shortcuts: Here’s where Back Tap becomes ultimately useful, at least if you can find or build the necessary shortcuts. Anything Shortcuts can do, you can invoke with a double or triple tap.
First you’re hearing of Shortcuts? How embarrassing! Read on. It’s an automation app that Apple includes with every iPhone. With it, you can chain together multiple actions derived from iOS capabilities or provided by your apps to create custom shortcuts. Other systems call similar collections of commands macros or automations or workflows.
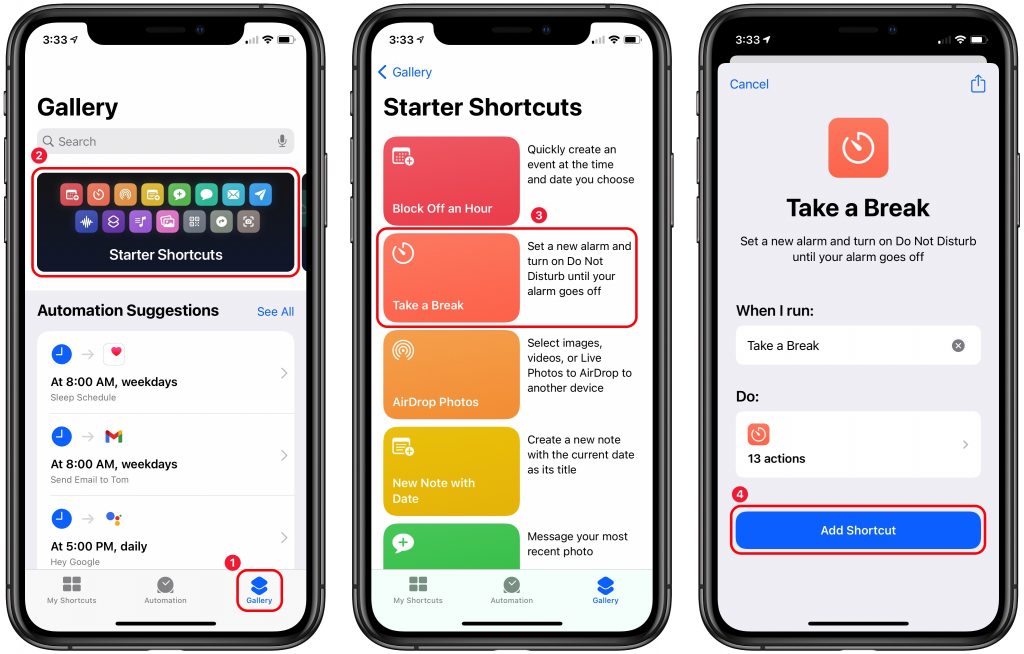
Explaining how to build your own shortcuts is a topic for another day, but you can also download sample shortcuts from Apple’s gallery, both to see how it’s done and to use them. For instance, if you tap the Gallery button in Shortcuts ➊, tap Starter Shortcuts ➋, tap Take a Break ➌, and tap Add Shortcut ➍, you’ll copy the Take a Break shortcut to My Shortcuts. Then you can assign a double tap in Back Tap to invoke Take a Break, which sets an alarm for a specified number of minutes and turns on Do Not Disturb until the alarm goes off.
If you want to learn more about Shortcuts right away, check out Take Control of Shortcuts, a 122-page ebook by Rosemary Orchard.
Give it a try! Back Tap might turn out to be the iOS 14 feature you use more frequently than any other.